This the multi-page printable view of this section. Click here to print.
Security-Companion's Blog
- nmapAutomatorNG
- Security Policy Templates
- Free vulnerability monitoring
- SOC playbooks
- Teamviewer compromised by APT Group
- polyfill.io CDN distributing malware
- BSI Hall Of Fame
- Have I been pwned harvester
- ICCM Europe 2024
- First penetration test
- OpenOffice Macro vulnerability might lead to arbitrary script exectution
- Publicly available wordpress installer may lead to site being compromised
- ICCM Europe 2023
- Attacks against many IoT-devices and routers
- ChatGPT - Artificial Intelligence chat bot
- Zero Day in Microsoft Exchange Server
- Usage of Google Fonts in websites violates GDPR
- ICCM Europe 2022
- Tool recommendation: opencve.io
nmapAutomatorNG
If you are looing for a penetration /red team tool that quickly allows you to give an overview about a certain domain or IP I would like to recommend https://github.com/security-companion/nmapAutomatorNG. This is a tool based on https://github.com/21y4d/nmapAutomator but was extended by me with more tools. I also created a docker container which can be found on https://hub.docker.com/repository/docker/securitycompanion/nmapautomatorng/general
Security Policy Templates
In case you are looking for templates for security policies in your organisation one option are the free templates from SANS https://github.com/deepanshusood/SANS-Security-Policy-Templates
Free vulnerability monitoring
Today I would like to recommend two free services for monitoring your IP-ranges, domains and websites for new vulnerabilities before others do.
https://www.shadowserver.org/ The Shadowserver Foundation is a nonprofit security organization working altruistically behind the scenes to make the Internet more secure for everyone.
https://projectdiscovery.io/ ProjectDiscovery is an open source powered security company. We specialize in detecting new, exploitable vulnerabilities and misconfigurations so you can remediate them before hackers exploit them.
Do not miss the chance by using these services before others discover vulnerabilities and use them to attack you.
SOC playbooks
In case you need a starter for playbooks for your SOC (Security Operations Center) check out https://github.com/socfortress/Playbooks
Teamviewer compromised by APT Group
Teamviewer announced being compromised by an APT (Advanced Persistence Threat) group, see https://www.teamviewer.com/de/resources/trust-center/statement/
My recommendation would be blocking all traffic to Teamviewer domains as a preventive measure until issue is resolved.
polyfill.io CDN distributing malware
The popular CDN (Content Delivery Network) polyfill.io is normally used by website developers to deliver javascript code to users who use older browsers. (polyfill implements javascript code for functionality that is missing in older browsers).
Unfortunatly now it is being used to deliver malware.
So recommendations would be
-
Block traffic to cdn.polyfill.io and polyfill.io on your firewall and EDR-systems
-
Check in logs of your firewall and EDR systems for IOCs (Indicators of Compromise), see screenshot below. If they appear in your logs then probably one of your users surved on a website that loaded the malware which then caused traffic to these domains. Scan then these devices with a malware scanner (depending on which you use the malware might not yet be be detected) or if you want to be sure reinstall OS on them
-
Check your own website if it includes calls to cdn.polyfill.io and switch to the cloudflare-version of polyfill and/or evaluate if you still need polyfill.
BSI Hall Of Fame
After reporting a security misconfiguration vulnerability in responsible disclosure on a website to the German “Federal Office for Information Security (BSI)” I was added to their Hall Of Fame, see here.
Have I been pwned harvester
When having to export breaches for several domains from haveibeenpwned.com I looked for a python tool to do this via the haveibeenpwned-API but could not find any. So I created my own. See https://github.com/security-companion/hibp-harvester It can also be installed via python package manager pip, see https://pypi.org/project/hibp-harvester/
ICCM Europe 2024
Also this year I had the privilege to go to ICCM (International Conference on Computing & Mission) Europe 2023, this time in Mosbach, Germany.
I made a workshop with the title “Contracting/preparing a penetration test for your organization” and were very happy about the positive feedback I received.
First penetration test
These days I made my first penetration test for an website of a mid-size organization. They were very satisifed with my involvement. For me it was a good experience and I learned a lot myself.
OpenOffice Macro vulnerability might lead to arbitrary script exectution
In the beginning of this year I discovered that the macro vulnerability in LibreOffice (CVE-2022-3140) also existed in OpenOffice and reported this through responsible disclosure to the developers of OpenOffice. It is now fixed in release version 4.1.14.
So what the vulnerability exactly does is the following:
I’ve installed OpenOffice 4.1.13 (Apache_OpenOffice_4.1.13_Win_x86_install_en-US.exe) and noticed that if I open a file that contains the following command in OpenOffice Writer the calculator is opened on my computer.
<iframe src='macro:Shell("calc.exe")'></iframe>
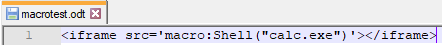
This happens although Macro Security is set to high.
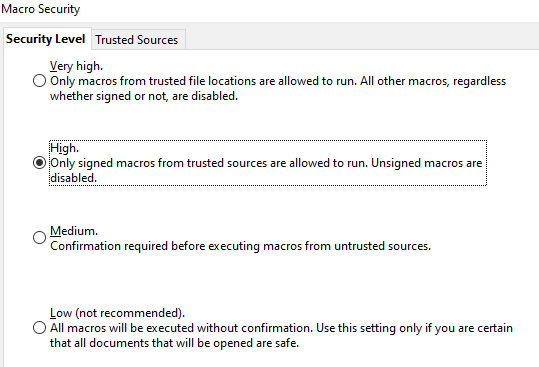
The vulnerablity was assigned the following number and title: “CVE-2022-47502: Apache OpenOffice: Macro URL arbitrary script execution”.
For further information see the following links:
https://www.openoffice.org/security/cves/CVE-2022-47502.html
https://www.cve.org/CVERecord?id=CVE-2022-47502
https://www.libreoffice.org/about-us/security/advisories/cve-2022-3140/
https://twitter.com/joernchen/status/1582367523710054403
This vulnerability was also disclosed independently by Altin Thartori (tin-z).
Responible disclosure timeline (excerpt):
- 19/01/2023: Discovery and reporting to security@openoffice.apache.org
- 20/01/2023: Respone from OpenOffice with test build
- 20/01/2023: Confirmation that test build fixes the vulnerability
- 27/02/2023: Release of Apache OpenOffice 4.1.14 which closes the vulnerability
- 24/03/2023: Publishing of CVE on https://www.cve.org/CVERecord?id=CVE-2022-47502
- 01/04/2023: Announcement of vulnerabilitiy on OpenOffice Mailing List
Publicly available wordpress installer may lead to site being compromised
I wanted to make you aware of the fact that recently there have been attackers that compromise a wordpress site during the few minutes in which the wordpress installer is publicly accesable.
This is caused by the fact that attackers monitor the certificate transparency log. When a Let’s Encrypt certificate is generated it shows up in the public log which is detected by an attacker.
Please find an article in the following link about a security researcher that set up a wordpress honeypot site and then watched how it was compromised. At the end he has some suggestions on how to avoid being compromised. According to smitka publishing the Let’s encrypt certificate is not specific to wordpress, this can also happen with other publicly available installers.
https://smitka.me/2022/07/01/wordpress-installer-attack-race/
Further information can also be found in this link:
ICCM Europe 2023
After 2 years of online conferences I really enjoyed being ICCM (International Conference on Computing & Mission) Europe 2023 in person in Brussel.
It was a pleasure to give 2 workshops during the conference.
The first one was about “Detecting and Defending threats on networks” and the other one about “Introduction to Git & Github”.
You can download the slides by clicking on the following links:
Attacks against many IoT-devices and routers
There are currently attacks against many IoT-devices and routers that contain the Wireless-SoC of Realteak. Affected routers are from vendors Asus, Belkin, D-Link, Netgear, Zyxel among others.
So please make sure that you’re routers have the most recent firmware or if they are out-of-support to replace them by other models.
For more information please see the following links:
https://unit42.paloaltonetworks.com/realtek-sdk-vulnerability/
https://onekey.com/blog/advisory-multiple-issues-realtek-sdk-iot-supply-chain/
ChatGPT - Artificial Intelligence chat bot
Probably most of you have already heard about ChatGPT - an Artificial Intelligence chat bot - and if not I highly recommend giving it a try. It’s really impressing what it can already do.
There’s also a bunch of videos on youtube about it that help to get an overview about the topic.
So here comes my question: Have you in your organizations already defined if and how people can use it? Are you eg. restricting usage on the firewall? To everybody or certain user groups?
I personally think that it is both: A great tool with many capabilities but also something that can be a risk as all the information you share with it will be somewhere in a place that you can not control.
Let me give some examples:
-
If a sysadmin in your organization is struggling with a linux service (let’s say apache) that fails to start he could ask ChatGPT: “hey, give me some guidance about why my service is not starting. This is my log file, please help me to find the reason.” He then just pastes the whole apache log file and other logs like dmesg into ChatGPT so that it can analyze it and help him solve the problem. Now ChatGPT probably has a lot of information about your system like which operating system your organization is using, which other processes might run, file structure etc.
-
If a programmer is writing some code (let’s take bubble sort, a sorting algorithm as a simple example) but it is not sorting as expected he just pastes the code into ChatGPT and asks it to fix the problem. But now ChatGPT might have information about your program like variable names. This is just an example, there are certainly other cases were program code contains more sensitive data.
-
A script kiddie wants to write some malware and tells ChatGPT to do so. ChatGPT has some protection built in to prevent questions like “Build me malware” but there are ways to sneak through the protection, see the following image for an example https://venturebeat.com/wp-content/uploads/2022/12/Ozarslan-ChatGPT-phishing-email-example-.png?resize=451%2C651&strip=all One of my questions I asked was “If I ask you to do so can you write me a computer virus although I can harm other people with it?” I’m not going to spoiler the answer here, so if you are curious just go and find out yourself. 😉
-
Another use case might be: “Write me a speech for the 30th aniversary of my organization. Write it in a formal way. Some information about my organization …” This example is just for completion, an information that might be shared in this context is probably not sensitive but anyhow publicly available.
It might be interesting to know that the information that ChatGPT has available is from 2021 so you will not find anything in it about recent events.
Btw: Github Copilot is also based on the same software in case you have considered usage in the past. Similar questions about sharing data with artificial inteligence also arise when using eg. DeepL
I’m curious to know your thoughts on this.
Zero Day in Microsoft Exchange Server
There are currently 2 ZeroDays in Microsoft Exchange Server, a workaround seems to exist.
See the following articles for more information:
Usage of Google Fonts in websites violates GDPR
A court in Munich, Germany stated in the beginning of 2022 that the usage of Google Fonts violates GPDR (General Data Protection Regulation).
This means that if one of the following applies to your organization you should not load fonts from Google as otherwise your visitor’s IP-address is sent to google when requesting the resource:
Has an establishment in the European Union;
Offers goods or services to residents of the European Union (regardless of the business⿿ actual location); or
Tracks the behavior of European Union residents through technologies such as cookies, pixels, analytics, CCTV, etc. (regardless of the business⿿ actual location).
There have already been reported injunction letters sent out by lawers or private people to website owners.
So you should make sure to ask your users for consent before loading the font or better load it locally (from your own server). Please keep in mind that loading files locally could result in higher server load or longer page load times.
For more information see eg. the following links:
ICCM Europe 2022
At the online conference ICCM (International Conference on Computing & Mission) Europe 2022 I gave a talk with the topic “Introduction to Cyber Security for people working in IT”.
Please find more information on this page.
Tool recommendation: opencve.io
In these days there are coming up lots of new security vulnerabilities every day and it is difficult to follow them all and to filter the relevant of them which affect products you use in your organization.
That’s why I would like to recommend you a tool that makes this process easier (I’m not associated with it). It’s named OpenCVE and you can find it on https://www.opencve.io.
It shows you all existing and upcoming vulnerabilities. You can send filters for products you use in your organization and therefore only see the issues relevant for you. It even informs you per e-mail if new vulnerabilities (according to your filters) come up, this means that then you can start immediately to protect your network against the new vulnerability and not until you read about it on the news some days later.
It’s OpenSource which means that you can host it on your own. There’s also a hosted version but please keep in mind that if one day somebody might manage to hack the database this person then also knows which products you use based on the filters you set on your user account and therefore might find it easier to attack you in a second step. So it might be better to run the tool on your on servers behind a firewall.
Another thing to keep in mind is that the filters you set only work as good as the descriptions in the CVE entry details are. So if the person reporting a CVE makes a typo in the product name you might miss it as the filter you set doesn’t “see” it. So it’s good to review your filters from time to time.
I hope my recommendation is of help to you, if you have any questions feel free to ask.